Monthly Cybersecurity Threat Intelligence Report - December - 2024


Executive Summary
December saw the public disclosure of information related to the Assad regime’s use of cyber surveillance to monitor and suppress opposition. The documents highlighted significant reliance on human intelligence and foreign surveillance technologies. Previously identified were state-sponsored espionage campaigns by Iran targeting regional officials through social engineering, phishing, and malware. Additionally, a targeted attack on the job portal job[.]sy delivered a Remote Access Trojan (RAT) to users' devices. Collectively, these developments underscore the urgent need for coordinated efforts across public, private, and governmental sectors to secure digital communications, protect civil liberties, and rebuild trust in new public institutions.
Introduction
This report provides an overview of significant cyber security incidents and trends observed in December. In the context of supporting a free Syria, we analyze key cyber activities impacting national security, privacy, and the integrity of information systems within and outside the region. Our findings are based on verifiable incidents and aim to assist in proactive defense and response to cyber threats.
Main Event: Cyber Surveillance Under the Assad Regime
 Figure 1 - Intelligence headquarters under the Assad regime and their security report storage methods
Figure 1 - Intelligence headquarters under the Assad regime and their security report storage methods
Detailed Analysis
Surveillance Techniques
- Communications Monitoring:
The regime implemented advanced surveillance technologies to intercept and analyse phone calls, social media activity, and broader internet use. A key technique was deep packet inspection (DPI), allowing detailed analysis of un-encrypted internet traffic to identify and track dissenting activities.
- Human Intelligence Operations:
A widespread network of informants played a pivotal role in surveilling Syrian citizens. These human sources worked alongside digital surveillance tools, providing a hybrid approach that combined cyber activities with real-world behaviour.
- Data Processing and Exploitation:
Collected data was systematically processed and analysed, albeit primitively, to create profiles used to target individuals for further suppression, including arrests and interrogations.
Imported Surveillance Technology
- Western Technology:
Technologies from companies such as Blue Coat Systems were used for internet censorship and traffic filtering, highlighting Western technology’s role in enabling the regime’s surveillance capabilities. Reports from sources like The Times and CBS News discussed the involvement of such technologies in supporting repressive regimes.
- Collaboration with Foreign Companies:
Companies such as Qosmos and Area SpA were implicated in supplying the regime with tools to monitor communications and enhance real-time surveillance capabilities, as reported by France 24 and Vice.
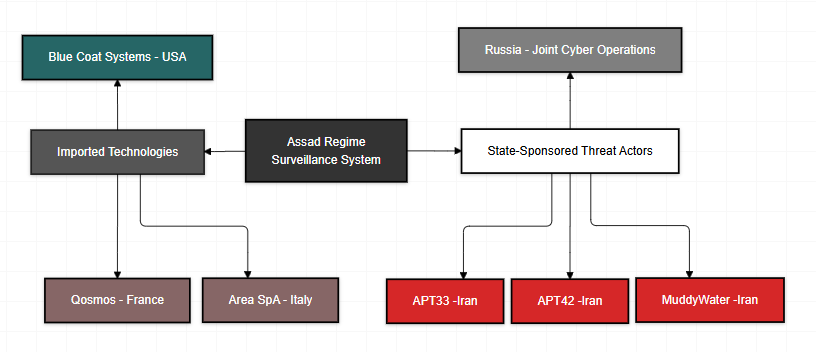 Figure 2 - Assad regime intelligence connections
Figure 2 - Assad regime intelligence connections
Operational Challenges
Documents revealed significant inefficiencies due to overlapping responsibilities among different security and intelligence branches.
Reliance on foreign technology highlighted a lack of local technical development, often leading to operational failures and security gaps.
Implications
These revelations carry profound implications for privacy and human rights, demonstrating how minimal technological resources, combined with widespread intelligence operations, can lead to significant abuses of individual freedoms. These events highlight the urgent need for robust cyber security measures and regulations, particularly in regions transitioning from oppressive regimes.
Case Studies
Case Study 1 - Iranian Cyber Espionage Campaign
Overview:
An Iranian Revolutionary Guard-linked cyber espionage group targeted national security officials through a cyber espionage campaign, utilising a fake HR company as a front.
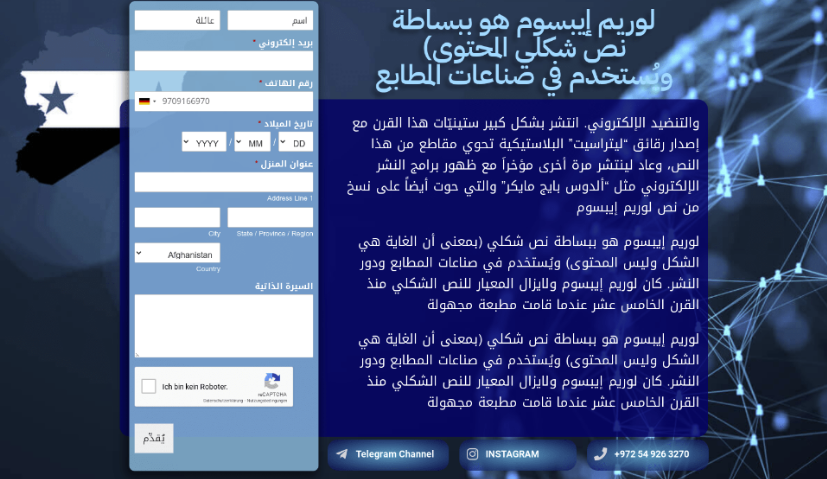 Figure 3 - Website used in the attack, translated into Arabic and incomplete
Figure 3 - Website used in the attack, translated into Arabic and incomplete
Detailed Analysis
Engagement Tactics
- Fake HR Company Website: The operation used a fake website, wazayif-halima[.]com, to pose as a legitimate HR entity targeting individuals in Syria and Hezbollah intelligence.
Attack Vectors
- Malicious Social Media Links: Distributed via profiles likely controlled by agents, targeting Syrian, Lebanese, and Iranian entities.
 Figure 4 - Social media campaign links used for distribution
Figure 4 - Social media campaign links used for distribution
- Data Collection on Website: Visitors were encouraged to input personal information, likely used for further intelligence gathering.
Operation Evolution
- Initial Stages: Arabic-language websites like "VIP Human Solutions" initially targeted Syrian intelligence and Hezbollah operatives.
- Later Stages: New websites, including "Optima HR," "Kandovan HR," and "Paras IL," focused heavily on Persian speakers, reflecting a shift towards internal priorities.
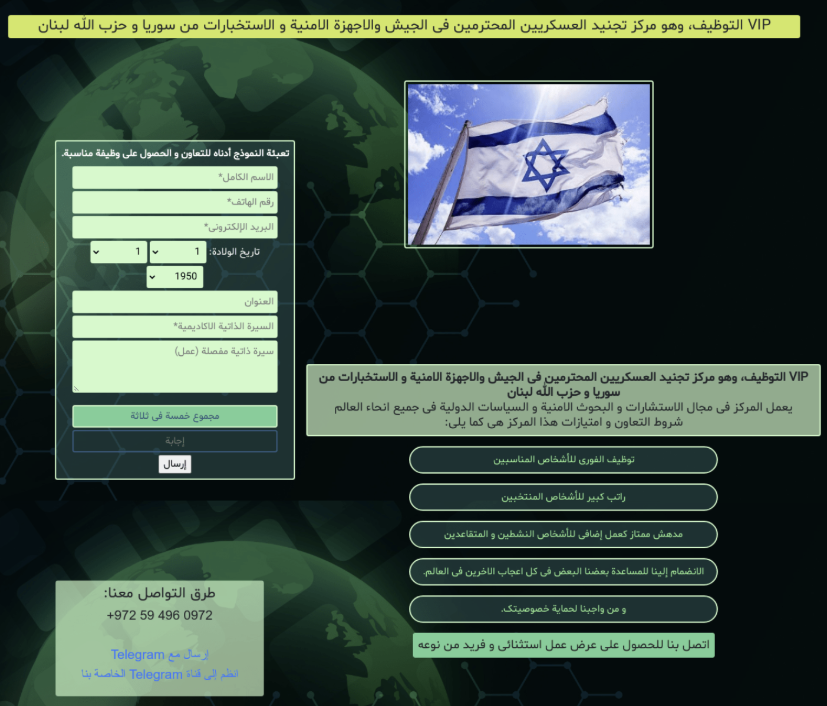 Figure 5 - Fake website used for gathering personal details
Figure 5 - Fake website used for gathering personal details
Case Study 2 - Targeted Cyber Attack on job[.]sy
Overview:
The job search platform job[.]sy in Syria was compromised, resulting in the deployment of a RAT Trojan and potential data leaks.
Detailed Analysis
Attack Techniques
- Website Redirect: Traffic was manipulated to redirect users to a malicious download page.
- Phishing Emails: Emails were sent from the official address info@job[.]sy, prompting users to download syriajob.apk.
Malware Analysis
- File Name: syriajob.apk
- SHA-256 Hash: 6390ba59d0c85d7db6de827b8cf829ca4db5123947d618bdeb17f7ee3a6c1c44
- Source: GitHub user intel2024, joined November, coinciding with the domain purchase of buggly[.]tech.
- Capabilities: Extensive permissions for data access, control functionalities, and further exploitation potential.
 Figure 6 - User account publishing the malicious app
Figure 6 - User account publishing the malicious app
Infrastructure and Domains
- Main Domain: buggly[.]tech
- Associated Subdomains: job.buggly[.]tech, demo.buggly[.]tech, job-admin.buggly[.]tech
- IP Addresses: Services hosted via Cloudflare, Amazon, and Google.
- Certificate Details: Registered under "Sleepy Welly, Dubai."
Recommendations
For the Public
- Exercise caution with emails and links from unknown or unexpected sources.
- Verify the authenticity of any communication or app download requests.
For Organisations
- Implement incident monitoring and response strategies to detect and address potential threats quickly.
- Regularly update systems to close security vulnerabilities.
For the New Syrian Government
As Syria transitions to a new regime, implementing cyber-security and privacy measures is essential. Below are some recommendations to establish a secure and transparent foundation:
1. Establish Secure Official Communication Channels
- Develop secure government communication platforms: Build official websites, portals, and email services with strong encryption (TLS/SSL, certificate pinning) and verified digital signatures.
- Enable Multi-Factor Authentication (MFA): Apply MFA on all government accounts to minimise the risk of account takeovers.
2. Manage and Analyse Archived Surveillance Data
- Secure the chain of evidence: Index and safely store documents or data recovered from previous surveillance systems to prevent tampering.
- Independent forensic analysis: Engage cyber-security experts and human rights organisations to analyse data methodically and provide insights into abuses.
3. Dismantle Repressive Surveillance Systems
- Identify and remove illegal technologies: Conduct audits of existing surveillance infrastructure and deactivate or remove systems used primarily for domestic repression.
- Public statements and transparency: Issue official notices detailing dismantled systems and the rationale, reinforcing the government’s commitment to human rights and privacy.
4. Lay the Foundation for Cyber-security and Privacy Legislation
Even under a transitional mandate, it is crucial to begin drafting cyber-security and privacy laws that protect citizens and uphold fundamental freedoms. A stable and trustworthy digital environment is key for the country’s future.
--------------------------------------------------------------------------
Appendix - Indicators of Compromise (IOCs)
Domains (Malicious/Associated Infrastructure):
- wazayif-halima[.]com
- beparas[.]com
- buggly[.]tech
- job.buggly[.]tech
- demo.buggly[.]tech
- job-admin.buggly[.]tech
Malware Files and Links:
- File Name: syriajob.apk
- SHA-256 Hash: 6390ba59d0c85d7db6de827b8cf829ca4db5123947d618bdeb17f7ee3a6c1c44
- Download Link: hxxps://github[.]com/intel2024/testplayground/raw/refs/heads/main/syriajob.apk
Associated Usernames and Hashes:
- WordPress Username: miladix
- Gravatar Hash: b7e2f4a5bc67256189e6732fbce86520
Communication Channels/Messages:
- hxxps://t[.]me/PhantomIL13
- hxxps://t[.]me/getDmIL
References:
- "Exposure of Assad Regime's Cyber Surveillance," The Times & The Sunday Times
https://www.thetimes.co.uk/article/syria-assad-secret-files-investigation-t5k0k2bnn - "Surveillance and Censorship: Inside Syria’s Internet," CBS News
https://www.cbsnews.com/news/surveillance-and-censorship-inside-syrias-internet/ - "Qosmos Allegations in Syrian Surveillance," France 24
https://www.france24.com/en/20120726-call-inquiry-french-firm-supplying-assad-regime-qosmos-surveillance-technology-ip-syria - "Area SpA Investigated for Selling Spy Gear to Syria," Vice
https://www.vice.com/en/article/gv5knx/italian-cops-raid-surveillance-tech-company-area-spa-selling-spy-gear-to-syria - "Iranian Cyber Espionage Operation," Reuters
https://www.reuters.com/technology/cybersecurity/iran-operated-fake-human-resources-firm-root-out-unfriendly-spies-researchers-2024-08-28 - "Syrian Hackers Distributing Stealthy C#-Based Silver RAT to Cybercriminals" The Hacker News
Syrian Hackers Distributing Stealthy C#-Based Silver RAT to Cybercriminals - "Spy With My Little Eye" Mandiant
I Spy With My Little Eye: Uncovering an Iranian Counterintelligence Operation | Google Cloud Blog